NIS2 Update November 2025
NIS2 Update November 2025
Welcome to the latest news about NIS2 and CyFun. Biggest news of the month is probably the launch of the new version of the CyberFundamentals Framework for NIS2 self-assessment (CyFun), dubbed CyFun 2025. This is a serious upgrade to match the NIST CyberSecurity Framework 2.0 (NIST CSF 2.0), and it also includes the latest knowledge and best practices in cybersecurity.
Major improvements are the increased focus on protecting the supply chain, on OT (Operational Technology) security, and the addition of governance measures.
No surprises here: supply chain security is a major challenge (just look at the Brussels Airport / Collins Aerospace cMUSE problem that crippled the operations in several airports), industrial security is lagging standard IT security in most organisations, and cyber governance is what triggers managers and board members.
Let's Get in Touch

Main section
Quick facts
/
CyFun 2025 Announced!
Latest updates about NIS2 and the CyberFundamentals Framework (CyFun):
CyFun 2025 Launched
The new version of CyFun was launched at one of CCB's NIS2 Connect and Share events with over 700 (!) participants.
Overall, the new CyFun 2025 framework is easier to use and understand. Full, updated information and guidance is available on the website CyFun.eu.
To make the switch easier, both CyFun® 2023 and CyFun® 2025 will be both available for a while. After that, only the new version will be accepted for self-assessments and third party conformity assessment.
"CyFun", short for “The CyberFundamentals Framework”, is now a registered trademark owned by the CCB. The use of the acronym CyFun® is authorised, as long as the source is clearly mentioned. It is based on NIST CSF 2.0, IEC 62443, ISO27001 and CIS Controls, also trademarked by their originators.
CyFun is still free of charge, and it also comes with a lot of tools and knowledge via the CCB and SafeonWeb websites, the CCB youtube channel, and the newest information is now consolidated on the new and colorful CyFun.eu website for CyFun 2025.
Although it originated in Belgium, it now has followers in Ireland and Romania, with other EU countries coming.
The most frequently asked question we get, is if CyFun is more suitable than ISO/IEC 27001 for organisations. The answer is not easy, but CyFun is probably better for smaller Belgian-scale companies, more practical and less complex, more action-oriented and an easier path to NIS2 compliance.
Danny Zeegers wrote a wonderful article about the new version called "The New Framework CyFun Essential 2025 - Evolution or Revolution", comparing it to CyFun 2023. Here are 5 of the most remarkable key findings:
- While about 70% of the previous measures were retained, the updated 30% bring a stronger focus on risk-based oversight, continuous improvement, and organizational maturity
- The number of key measures related to incident management has doubled
- Controls focused on supplier and supply chain security have doubled
- The number of governance controls expanded dramatically (from 8 to over 20)
- The 2025 edition introduces OT-specific guidelines within each domain
Summarizing this: "The CyFun 2025 update is a revolution in mindset, shifting cybersecurity from a technical checklist to a core business governance function". (thx Danny Zeegers)
NIS2 Transposition Status & Tracker
You can find the current status of implementation as reported by EU Member States on the public NIS2 transposition tracker of the European Commission.
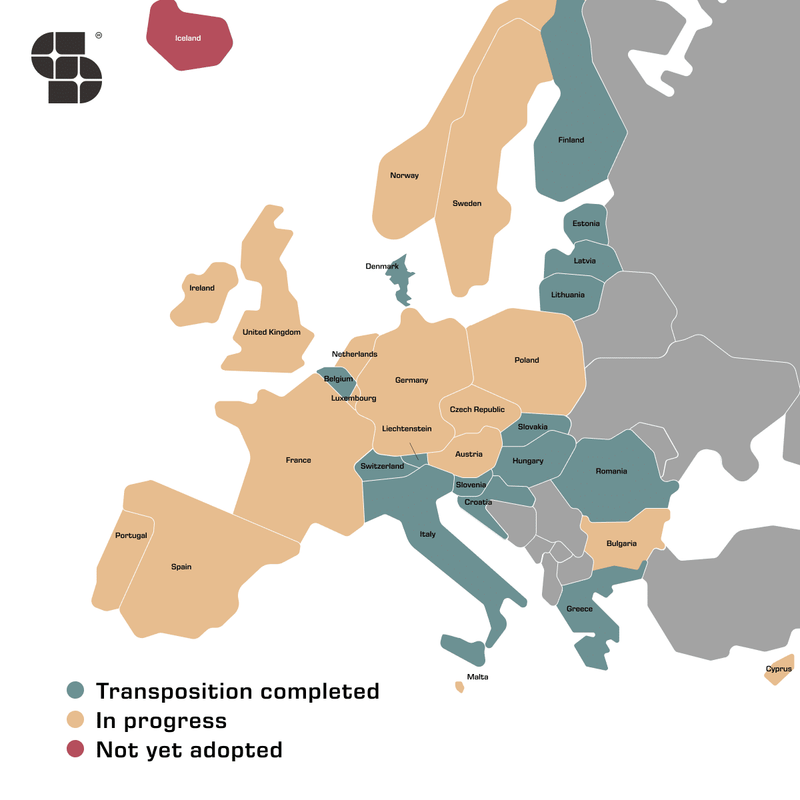
As you can see via this page, even a year after the transposition deadline, several countries are not ready. The European Commission sent a "reasoned opinion" to 19 member states, including the biggest countries France, Germany and Spain, but also the Netherlands. The Dutch government has publicly indicated that the implementation of the NIS2 legislation into the national Cybersecurity Act ("Cyberbeveiligingswet (Cbw)", which will replace the current NIS Act, the "Wet beveiliging netwerk- en informatiesystemen (Wbni)") is delayed (again). Despite the legislative delay, authorities are urging companies not to wait, and have published some of the new incident reporting rules and risk management obligations. Their Auditdienst Rijk and the IT auditor organisation NOREA have released the Cbw (NIS2) Control Framework but I strongly invite them to take a look at the more extensive CyFun 2025 framework.
The Commission requests immediate action by the countries that are not ready with their transposition, and it may decide to refer the cases to the Court of Justice of the European Union when these countries stay unresolved and thus noncompliant.
Another great NIS2 transposition tracking website can be found at Secomea, a change leader in manufacturing security. See map of Europe below. Another status report can be found at the OpenKRITIS website.
As it is no longer part of the EU, the UK is finalising a regulation similar to NIS2, the Cyber Security & Resilience Bill, and you can find a good comparison here and here. Unfortunately, its approval was delayed again in September 2025.
The German NIS 2 Implementation Act (formerly NIS2UmsuCG) that transposes the NIS 2 Directive into German law, was passed by their Cabinet on 30 July 2025 and should come into force in 2025.
So, while NIS2 is "in force" at the EU level, it is not "enforceable" in all countries. L'union fait la force, but there is no united cybersecurity law.
Perhaps the EU should have made it a regulation, a uniform and immediately applicable law across the EU, and not a directive, which allows each country to choose how to implement (transpose) it through its own national laws. A choice between 1 giant discussion at EU level or 27 big discussions at national levels.
NIS2 Makes Secure Supply Chains Mandatory
NIS2 also wants to address supply chain risks. Companies should understand their supply chain and know their sub-suppliers. A best practice is to conduct audits and crisis exercises with suppliers. Additional measures would be to integrate SLAs on security, updates, sharing of sensitive data and incident management into contracts, and review the risk analysis at least annually.
We can see the extra focus on supply chains in CyFun 2025. Exact measures differ between important and essential supply chain partners but you can find the assessment questions in sections GV.SC-05-10 of CyFun 2025.
A very well-known example of supply chain security problems was Brussels Airport. It was hit by a massive cyber attack in September, causing flight delays and cancellations, due to a ransomware attack at external service provider Collins Aerospace. This shows how vulnerable companies are these days when one of the partners in their information supply chain gets compromised. As expected, Brussels Airport is now looking at a replacement for Collins aerospace. A good background article can be found on the Industrial Cyber website.
Strengthening OT Security
There is also more focus on OT security in the new CyFun 2025, but it is mainly done by adding "/OT" to certain measures such as GV.OC.04.4, which says that "Recovery time and recovery point objectives (RTO/RPO) for the resumption of essential ICT/OT system processes shall be defined and monitored". Sirris has a good article of the various CyFun measures to address the security of connected sensors, smart machinery, robots, OT/IoT devices, ... in production and manufacturing systems.
At Howest, we are very happy with the increased focus on OT Security, as industrial/OT security is one of our key knowledge areas, and we have a very special interest in maritime (ships) and offshore (wind, solar, tidal and water power energy) cybersecurity, both pretty critical sectors.
Sidenote: People who are not familiar with RTO and RPO should check out this TechTarget article. Anyway, it is good that companies are forced to think about business continuity, backup and disaster recovery planning, which can also be infringed by supply chain attacks.

First CyFun Certification Body
On September 4th, Brand Compliance België became the first certification body to receive CyberFundamentals accreditation from BELAC for conducting CyFun verification. As their Chief Compliance Officer stated it: "For Belgian organizations that are serious about their digital resilience, now is the time to start implementing CyberFundamentals".
Links with the CRA
Together with the Cyber Resilience Act (CRA), NIS2 should force us to adopt a "security by design" and "resilience by default".
While NIS2 focuses on the operational security of essential services, CRA focuses on the security of products of digital elements (PDEs). Its goal is very different as it is mainly aimed at manufacturers, importers, distributors of hardware and software to ensure that their digital products placed on the EU market are "secure by design," have default security settings, and receive long-term security updates. So, some innovative companies will also have to tackle the CRA once they have finished their NIS2 compliance work. With the Data Act and the AI Act also on their plate, it sometimes looks like there is no end to EU regulation.
Talking about the CRA, there is a great resource (albeit not an EU official one) at https://www.cyberresilienceact.eu with the full text, explanations, videos, fast checks, compliance checklists, news, and more info about CE marking. We also found great CRA information resources at the Open Source Security Foundation website. And yes, the CRA does apply when open source software (OSS) is put on the market as part of a commercial activity, making that commercial entity the "Manufacturer", although some people still think and believe open source software is exempt of CRA.
As there is more and more attention for CRA, we are planning a Tech & Meet information session at Howest University of Applied Sciences to explore the CRA.
Also at Howest, we are turning the CyFun 2023 framework into a user-friendly multilingual tool which is much easier to use than the spreadsheets. Of course our NIS2Ready tool has import and export capabilities, and a nice spider chart showing discrepancies and non-compliance. The CyFun 2023 to CyFun 2025 mapping also allows us to import "legacy" data into our CyFun 2025 tool. Furthermore, we are adding extra knowledge like CCB's CyFun 2025 Maturity Level Use Cases as well as best practices based on our CyberSecurity education at Howest.
Bottom section
Extra Resources
- The official website for CyFun 2025 is the colorful CyFun.eu
- One of the best information sources is the CCB's YouTube channel, with videos on cybersecurity, cyber attacks, ransomware, NIS2, CyFun, ...
- As we are extremely good cyber friends with Ireland these days, it is worth mentioning their National Cyber Security Center (NCSC) NIS2 page with a report on Risk Management Measures and Guidance (RMM)

- Bridging the NIS2 Cyber Security Gap by Aon, one of the bigger risk insurance companies
- Structured Cybersecurity Incident Reporting under NIS2 by Harry VM van der Plas and Danny Zeegers
- NIST CSF 2.0 - the original NIST CyberSecurity Framework was released in 2014, and got a major upgrade in 2024 with CSF 2.0 when the 6th core function "Govern" was added to the other 5 core functions (Identify, Protect, Detect, Respond, Recover). All of these functions are clearly represented in the CyFun 2025 framework.
- DORA and NIS2 compared
- ETSI Technical Report "Critical Security Controls for NIS2"
- EU Cybersecurity Directive Playlist by Cyen
- How can SMEs remain resilient in accordance with NIS2?
- CyFun 2025 Maturity Level Use Cases
- ENISA Advisory Group opinion paper on NIS2 Directive Post-Implementation
- Is Your Organization Ready for NIS2 Directive Compliance? (Responsum)
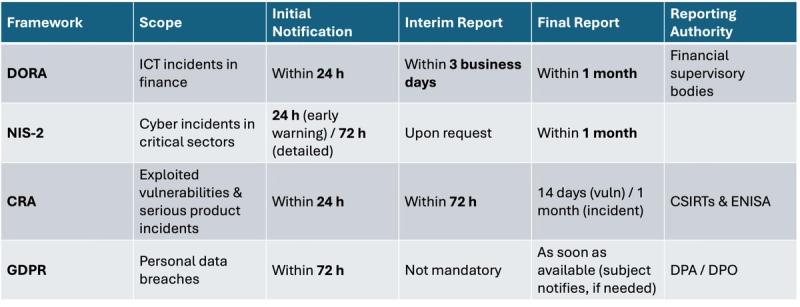
Finally, I would like to advise you to build a streamline multi-regulation (NIS2 / DORA + CRA + GDPR) incident reporting pipeline that handles all EU regulations & directives where incidents have to be done quickly and swiftly to be compliant. More info in this LinkedIn post.
Contributors
Authors
/
Patrick Van Renterghem, AI, CyberSecurity, Web3, Immersive Tech, Quantum, ... Community Builder & LLL Coordinator
Want to know more about our team?
Visit the team page
Last updated on: 11/13/2025
/
More stuff to read




