Behind the Hack: the Unlocked Storage Container
Behind the Hack: the Unlocked Storage Container
A public dirt road led us straight to an unlocked storage container - inside was direct access to an OT network. By simply plugging in a cable, we found and rebooted a PLC, stopping a crane without any alerts.
No passwords, no monitoring, no barriers. This case shows how physical access equals total system access. The fix? A smart lock, fencing, and cameras. A reminder that sometimes hacking just means finding the door that’s already open. Simple measures can stop real threats.

Main section
Quick facts
/
We hacked a crane... by opening a door
/
No malware. No phishing. Just bad physical security
/
Sometimes hacking is as easy as... walking in
One container + one cable = crane shutdown
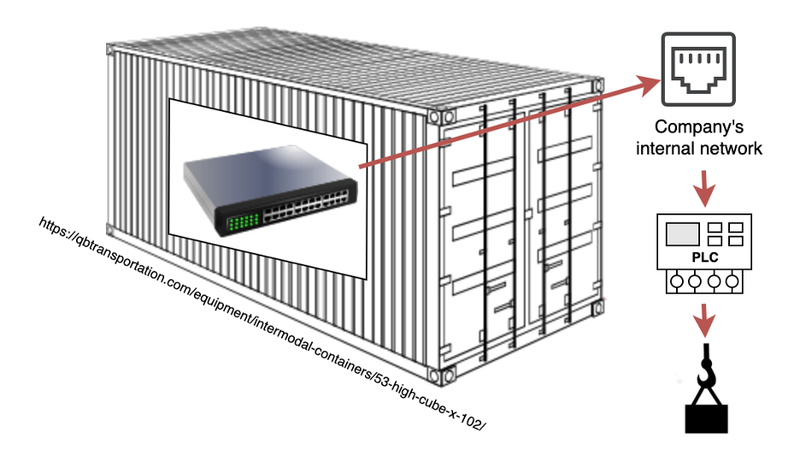
It started with something deceptively simple: a walk down a public dirt road. No gates. No signs. No fences. Just open access to an industrial site. There, sitting in plain sight, was a white storage container. It looked harmless—maybe even forgotten.
But when we opened the door (which wasn’t locked), we found something serious inside: a network switch. In layman’s terms, a switch is like a central connector for computers and machines to talk to each other. This one was part of the Operational Technology (OT) internal network—the very system that controls machinery on-site.
No passwords. No surveillance. No alerts. So we did what any attacker could do: we plugged in a standard Ethernet cable.
Within moments, we were inside the OT network.
Once connected, we ran a basic network scan—nothing sophisticated. Just enough to see which devices were active. Among them, we found an old PLC (Programmable Logic Controller). PLCs are the brains behind many industrial machines. This one was running without updates, without protections, and without any checks on who could talk to it.
We crafted a simple command to restart the PLC. And when the PLC rebooted, it temporarily stopped the nearby crane it was controlling.
In other words:
- We shut down part of the operation…
- Without using any malware…
- Without triggering alarms…
- Without ever being challenged.
No need for fancy tools. No passwords to crack. Just a wide-open door—both literally and digitally.
This wasn’t about elite hacking skills. It was about basic security hygiene being completely ignored.
Bottom section
The Solution: From Sitting Ducks to Fortified Zones
To their credit, the company took the breach seriously. Here’s how they fixed it:
✅ Smart lock installed on the container door. No more easy entry.
✅ Perimeter fencing added around the facility to prevent direct access from public areas.
✅ Surveillance cameras deployed in isolated and critical spots. Now, any unusual activity gets noticed.
These are not expensive, complex cybersecurity tools. These are common-sense physical controls that any company can implement.
Key Takeaways: Simple measures can lead to much more protection
What can we all learn from this?
- 🛠️ Physical access = total access. If someone can plug in, they can probably control or shut down your systems.
- 🚪 Outdoor cabinets, containers, and network closets are critical assets - secure them like you would your server room.
- 🔒 Use deterrents: visible cameras, warning signs, locks, fences. Even basic obstacles make a difference.
Most attacks don’t look like Hollywood hacking scenes. Sometimes, they’re as boring - and as dangerous - as someone walking in with a cable.
“Hacking often starts by finding the door that’s already open.”
Let our students or researchers help you find and lock those doors - before someone else does. Do not hesitate to contact us with your cybersecurity questions!
Finally: if you want to be informed about our cybersecurity updates, be sure to follow Howest Cyber3Lab on LinkedIn.
Contributors
Authors
/
Patrick Van Renterghem, AI, CyberSecurity, Web3, Immersive Tech, Quantum, ... Community Builder & LLL Coordinator
/
David Prada, Onderzoeker op het gebied van cyberbeveiliging
Want to know more about our team?
Visit the team page
Last updated on: 7/9/2025
/
More stuff to read




