Behind the Hack: the Conference Room Laptop
Behind the Hack: the Conference Room Laptop
This is the story of a public guest laptop in a conference room where they offered hands-on product demos. It became the gateway for a full-scale corporate breach by our ethical hackers.
The servers were secured. Employees used strong passwords. The network had a firewall. Still, our ethical hackers got into their internal network and uncovered some partial formulas to create their products. Highly interesting for their competitors.

Main section
Quick facts
/
A single public laptop can open all the doors
/
Enforce network segmentation, separate IT from OT
/
Use non-admin guest accounts for public devices!
/
The keys to the company secrets were in plain sight
The story of a public laptop that opened all the doors to the internal corporate network
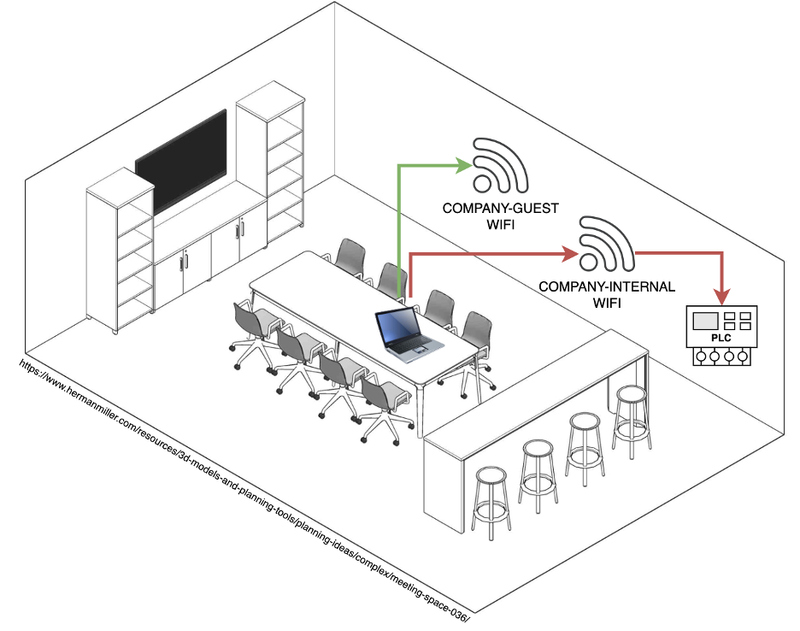
In a company that prides itself on offering hands-on product demos, a simple guest laptop in a conference room turned into the gateway for a full-scale corporate breach.
Let’s walk through how easily it all unraveled.
The company allowed visitors to use a meeting room to test their solutions. In the room, there was a "public" laptop with a handy login password stuck right on a sticker on the casing.
Convenience over security, the customer is king.
Once logged in, we had local admin rights. That meant we could run system-level commands without breaking a sweat. Here’s what we did:
- We listed saved Wi-Fi networks:
netsh wlan show profiles - We pulled the clear-text password for the internal corporate Wi-Fi:
netsh wlan show profile name="COMPANY-INTERNAL" key=clear - We connected to their internal corporate IT network and got full access
From there on, we got excited and it only got worse for the company.
We scanned the network and found a PLC (Programmable Logic Controller) that they were using for product testing. It still used default credentials - and it contained proprietary formulas to create their products.
In just minutes, a visitor became a corporate spy. And all it took was a public laptop, a bit of curiosity and some basic skills that you learn in the first year of any Cybersecurity course.
This is not fiction. This is real.
This is how we hacked you.
Bottom section
Why it matters and how you can fix this
Simple measures can already have a big impact. Of course, it is better to take these measures before something happens.
Security isn’t always about expensive tools or complex systems. It often starts with basic hygiene - and fixing the small cracks that let intruders walk in.
Here’s what the company did right after the breach:
✅ Removed saved Wi-Fi profiles from public devices
✅ Revoked admin rights on all shared laptops
✅ Changed the default credentials on critical OT devices like PLCs
And here’s what every organization should do before it’s too late:
Your Minimum Action Plan:
- Use non-admin guest accounts for any public or shared machines
- Set laptops to auto-clean browsing history and saved credentials
- Enforce network segmentation – separate IT from OT using VLANs
- Audit and update device credentials (especially for PLCs and IoT)
- Don’t allow public devices to store sensitive network data
🧠 One overlooked device can bring your entire system down.
Start with basic awareness. Follow up with simple, effective safeguards. Because in cybersecurity, small oversights can open big doors.
Small cracks can lead to big breaches - and small steps can prevent them.
If you want our ethical hackers or our students to visit your company and see where those small cracks are, do not hesitate to contact us. Of course, our researchers can also help with the more advanced aspects of cybersecurity, from IT/OT segmentation, network monitoring, incident response planning procedures, ... to getting NIS2-compliant.
Finally: if you want to be informed about our cybersecurity updates, be sure to follow Howest Cyber3Lab on LinkedIn.
Contributors
Authors
/
Patrick Van Renterghem, AI, CyberSecurity, Web3, Immersive Tech, Quantum, ... Community Builder & LLL Coordinator
/
David Prada, Cybersecurity Researcher
Want to know more about our team?
Visit the team page
Last updated on: 7/9/2025
/
More stuff to read




