Behind the Hack: How Audio Visual Equipment like ClickShare became a Hacker's Gateway
Behind the Hack: How Audio Visual Equipment like ClickShare became a Hacker's Gateway
In a recent ethical hacking project, we gained full access to a company’s internal network... by simply plugging our laptop into their ClickShare assigned Ethernet port in one of their conference rooms. This gave us complete access and a quick scan exposed vulnerabilities leading to full control.
So, simple conference room equipment can compromise your entire network, even though you invested heavily in firewalls, antivirus software, and employee training.
Let that sink in. No need for phishing emails. No password cracking. No high-tech wizardry. Just a cable, a laptop, and access to a conference room.

Main section
Quick facts
/
We hacked a company by booking a meeting room and unplugging a projector
/
The weakest link in your cybersecurity might be hiding behind the screen
/
Old vulnerabilities never die - they just wait in forgotten servers
/
Is your conference room a hacker's paradise?
This is how we hacked the company from their meeting room
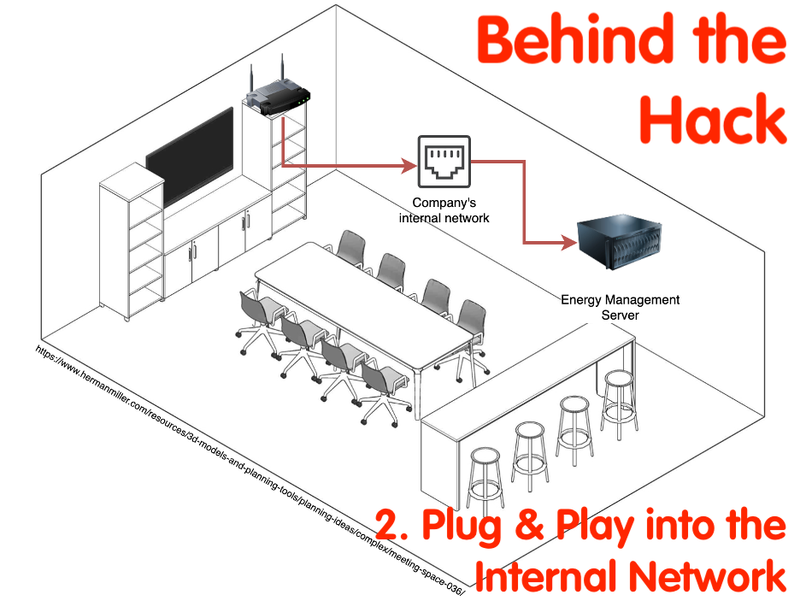
Here's what we did:
- We booked a meeting room just like any visitor might.
- Inside, we found a ClickShare device connected via a standard Ethernet cable.
- We unplugged the device, connected our own laptop – and were instantly inside the internal corporate network.
- A quick scan revealed an HPE ILO 4 server, running old firmware vulnerable to CVE-2017-12542.
- We exploited that flaw to create our own administrator account, bypassing their current credentials
- Within minutes, we had remote power control over their other servers.
Let that be a lesson: Your weakest link might be hiding behind your projector.
Conference technology is often overlooked in security settings. The people who install it are happy when it works, and may create security holes to do so.
Devices like ClickShare can become direct bridges into sensitive systems if not properly segmented. Disclaimer: when properly secured, Barco ClickShare is an outstanding product, we also use it.
Bottom section
From Vulnerability to Visibility: What You Can Do Today
The good news? A few smart actions can turn this from a major risk into a non-issue.
Here’s what the company did after our test:
- They physically locked away AV equipment to prevent tampering.
- They isolated the AV (Audio Visual) network onto a separate VLAN – away from core systems.
- They reviewed and limited ClickShare integration options (with help from the vendor).
- They updated their HPE ILO firmware to close the known vulnerability.
What you should do:
✅ Segment AV equipment: Use a separate VLAN for any presentation or demo gear.
✅ Restrict access: Block any unknown or unmanaged devices from reaching your internal systems.
✅ Lock it down: Physically secure network ports and devices in shared spaces.
✅ Stay updated: Even lesser-used servers and hardware need security patches. Actually, the least visible and most forgotten may become the most dangerous.
💡 Remember: if your conference gear connects to your core systems… so can anyone else.
Cybersecurity isn't only about firewalls or encryption. It's about not leaving a live Ethernet cable waiting for someone with bad intentions.
Want to stay ahead of these threats? Start by walking through your office with the eyes of a hacker. Invite a student or a researcher from Howest University of Applied Sciences to take an ethical hacker's view on your network.
Do not hesitate to contact us with your cybersecurity questions! Also, if you want to be informed about our cybersecurity updates, be sure to follow Howest Cyber3Lab on LinkedIn.
Contributors
Authors
/
Patrick Van Renterghem, AI, CyberSecurity, Web3, Immersive Tech, Quantum, ... Community Builder & LLL Coordinator
/
David Prada, Cybersecurity Researcher
Want to know more about our team?
Visit the team page
Last updated on: 7/9/2025
/
More stuff to read




